Nowadays, Authentication is a critical function in modern applications, serving as the gateway to safeguard data and resources. In this chapter, we will focus on JWT Authentication (Detail: RFC 7519 and JWT IO)
Let’s say you’re part of a founding team or have just joined an early-stage company. The main focus should be building the product for your customers. Building authentication from scratch is complex and error-prone, start to leverage existing solutions. Authentication goes beyond basic features like email login, OTP, or social sign-ins; it requires robust, up-to-date security measures to minimize risks and protect your users.
You can uses some of options:
- Firebase Authentication
- AWS Cognito
- Supabase Authentication
- Auth0
Most of these services use JWT. JWTs allow you to authenticate users without maintaining a session on the server (stateless). The token contains all the necessary information, making your system scalable and reducing server overhead. The token can be easily validated on the client or server side without needing a database lookup, which speeds up authentication processes.
Before diving deep into a discussion on JWT, let’s start with application architecture. I’ll use Firebase Authentication as an example.
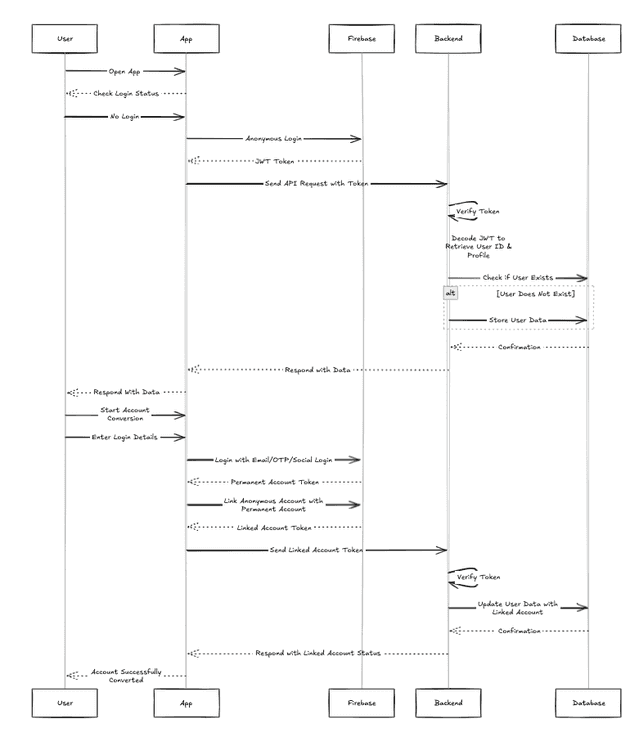
Firebase Authentication simplifies user authentication with support for email, OTP, and social logins like Google and Facebook. The best part is anonymous login (thanks for stateless JWT architecture).
Anonymous Login
Users can access our app without logging in, and they can later upgrade their anonymous accounts to permanent ones without losing data or progress. By allowing quick access, you increase the chances that users will stay and engage with your product.
The signing process, whether anonymous or not, happens on the client side using the Firebase SDK. Our backend only verifies the token sent by the client when the client makes a request to the backend API. Additionally, the backend can verify the user ID in the JWT body. By decoding the token, the backend can access the basic user profile.
The flow may looks like:
Please note, extracting information from the token body and storing it in your database depends on your use case. Your app might not need to store anonymous users.
JWT Token Verification
Our backend ensures that every request is legitimate traffic, preventing unauthorized access such as bots or abusers from accessing our data through the API.
Before continuing, let's take a deeper dive into how a JWT token is generated. Basically, JWT uses two types of keys: a public key and a private key.
- The private key is a confidential key used exclusively by the token issuer (e.g., the backend server). Its primary role is to sign the JWT and ensure that the token is authentic and hasn't been tampered with.
- The public key is a non-confidential key that is shared openly with clients or other services. It is used to verify the JWT’s signature.
With the Firebase SDK, your backend doesn’t need the private key since Firebase signs the tokens. Firebase provides a public key (via the JWKS URL) for verifying token signatures. For providers without SDK support, you can manually verify JWTs using the issuer’s public key to ensure validity and integrity.Learn more.
Most third-party providers offer a public signing key for token verification, which can be easily integrated or used with their SDK. This documentation highlights a different approach: JetProxy JWT Auth Middleware.
In conclusion, building authentication from scratch is complex and time-consuming. Leveraging third-party solutions like Firebase Authentication, AWS Cognito, Supabase, or Auth0 allows you to focus on your core backend while ensuring robust, scalable, and secure authentication. By integrating these services, you can streamline the authentication process, reduce server overhead, and enhance your application's security and user experience.